Cloud
Provisioning on AWS
Guide for deploying Jobs or Services to AWS.
This guide will walk you through the process of creating a User Account and IAM Role creationservice principal in AWS that you can use with Outpost.
PREREQUISITES
Create a User Account
AWS accounts can be attached with a policy that limits the permissions of the account. Follow these steps to create an AWS user with the minimum permissions required by Outpost:
- Open the IAM dashboard in the AWS console and click on the Users tab. Then, click Add users and enter the user’s name. Click Next.
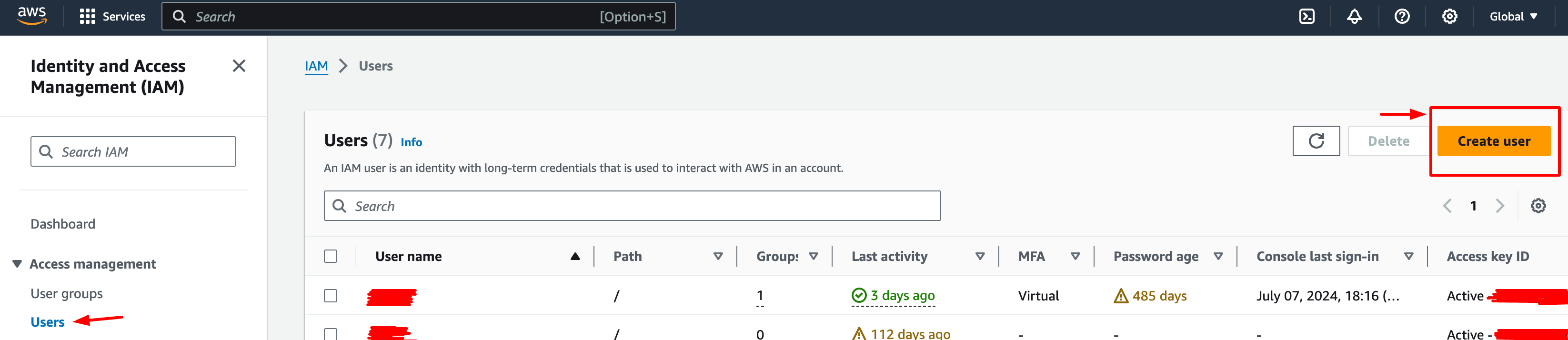
Create User screen on the AWS Dashboard
- In the Permissions options section, select "Attach existing policies directly"; Click on the Create Policy. This opens another window to create an IAM policy.
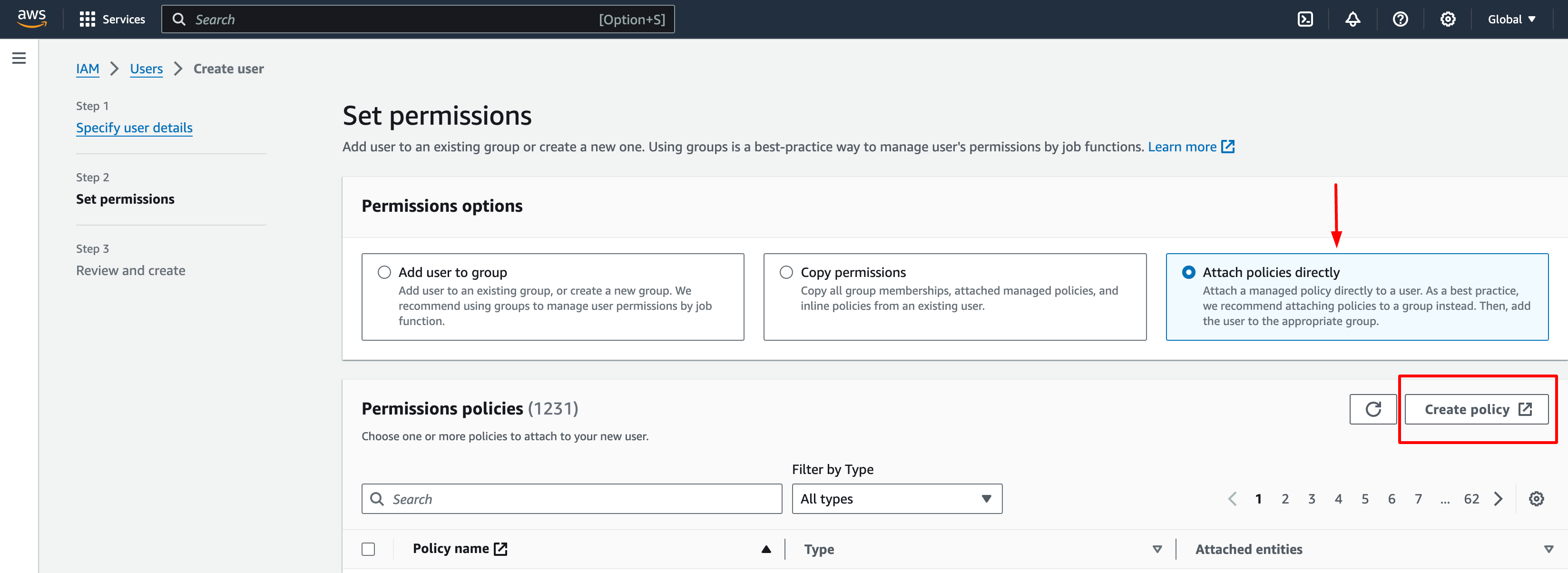
Add Permissions to User screen on the AWS Dashboard
- Choose "JSON" tab and place the following policy into the box. Replace the
<account-ID-without-hyphens>with your AWS account ID. You can find your AWS account ID by clicking on the upper right corner of the console.
1{
2 "Version": "2012-10-17",
3 "Statement": [
4 {
5 "Sid": "VisualEditor0",
6 "Effect": "Allow",
7 "Action": "ec2:RunInstances",
8 "Resource": "arn:aws:ec2:*::image/ami-*"
9 },
10 {
11 "Sid": "VisualEditor1",
12 "Effect": "Allow",
13 "Action": "ec2:RunInstances",
14 "Resource": [
15 "arn:aws:ec2:*:248635546921:subnet/*",
16 "arn:aws:ec2:*:248635546921:instance/*",
17 "arn:aws:ec2:*:248635546921:network-interface/*",
18 "arn:aws:ec2:*:248635546921:security-group/*",
19 "arn:aws:ec2:*:248635546921:volume/*"
20 ]
21 },
22 {
23 "Sid": "VisualEditor2",
24 "Effect": "Allow",
25 "Action": [
26 "ec2:TerminateInstances",
27 "ec2:DeleteTags",
28 "ec2:StartInstances",
29 "ec2:CreateTags",
30 "ec2:StopInstances"
31 ],
32 "Resource": "arn:aws:ec2:*:248635546921:instance/*"
33 },
34 {
35 "Sid": "VisualEditor3",
36 "Effect": "Allow",
37 "Action": "ec2:Describe*",
38 "Resource": "*"
39 },
40 {
41 "Sid": "VisualEditor4",
42 "Effect": "Allow",
43 "Action": [
44 "ec2:AuthorizeSecurityGroupIngress",
45 "ec2:CreateSecurityGroup"
46 ],
47 "Resource": "arn:aws:ec2:*:248635546921:*"
48 },
49 {
50 "Sid": "VisualEditor5",
51 "Effect": "Allow",
52 "Action": [
53 "ec2:DeleteSecurityGroup",
54 "ec2:ModifyInstanceAttribute"
55 ],
56 "Resource": "arn:aws:ec2:*:248635546921:*"
57 },
58 {
59 "Sid": "VisualEditor6",
60 "Effect": "Allow",
61 "Action": "iam:CreateServiceLinkedRole",
62 "Resource": "*",
63 "Condition": {
64 "StringEquals": {
65 "iam:AWSServiceName": "spot.amazonaws.com"
66 }
67 }
68 },
69 {
70 "Sid": "VisualEditor7",
71 "Effect": "Allow",
72 "Action": [
73 "iam:GetRole",
74 "iam:PassRole"
75 ],
76 "Resource": "arn:aws:iam::248635546921:role/seedling-v1"
77 },
78 {
79 "Sid": "VisualEditor8",
80 "Effect": "Allow",
81 "Action": "iam:GetInstanceProfile",
82 "Resource": "arn:aws:iam::248635546921:instance-profile/seedling-v1"
83 },
84 {
85 "Effect": "Allow",
86 "Action": [
87 "iam:GetRole",
88 "iam:PassRole",
89 "iam:CreateRole",
90 "iam:AttachRolePolicy",
91 "iam:PutRolePolicy"
92 ],
93 "Resource": [
94 "arn:aws:iam::248635546921:role/seedling-v1"
95 ]
96 },
97 {
98 "Effect": "Allow",
99 "Action": [
100 "iam:GetInstanceProfile",
101 "iam:CreateInstanceProfile",
102 "iam:AddRoleToInstanceProfile"
103 ],
104 "Resource": "arn:aws:iam::248635546921:instance-profile/seedling-v1"
105 }
106 ]
107}-
Click Next: Tags and follow the instructions to finish creating the policy. You can give the policy a descriptive name, such as
outpost-policy. -
Go back to the previous window and click on the refresh button, and you can now search for the policy you just created.
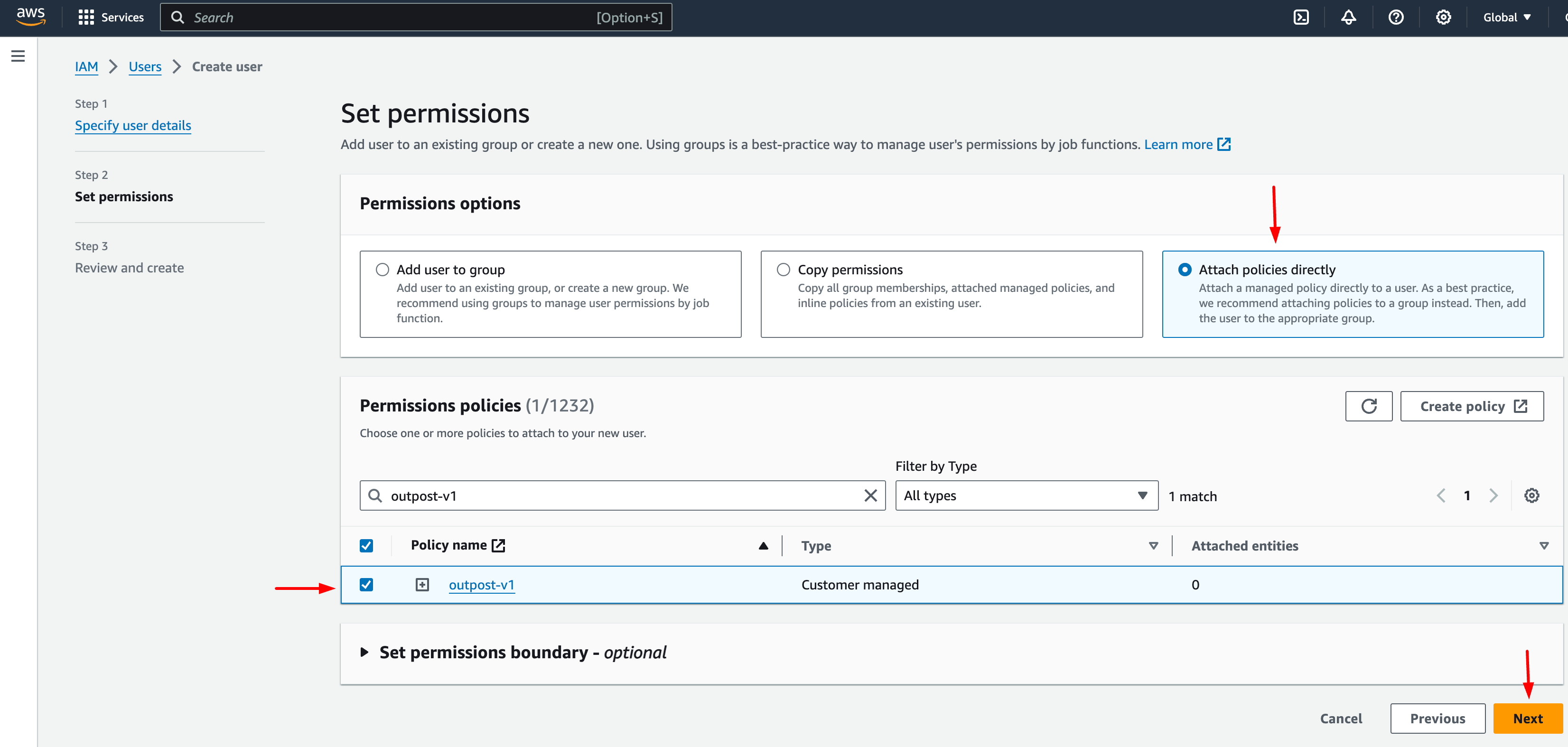
Verify the added policy Permissions to User screen on the AWS Dashboard
- Click on Next and follow the instructions to create the user.
With the steps above you are almost ready to have the users in your organization to use Outpost with the minimal permissions.
One more thing to do is to create a single IAM role outpost-v1 for all users in your organization. There are two ways to accomplish this:
- Add additional permission for the user you created to allow Outpost to automatically create the IAM role using the user account. You can modify the last two rules in the policy you created in step 4 with the highlighted four lines:
If you have created the policy, you can find the policy in the Policies tab in the IAM dashboard. Click on the policy outpost-policy (or the name you set in step 4) and click on the Edit to edit the policy.
1:emphasize-lines: 6-7,17-18
2
3 {
4 "Effect": "Allow",
5 "Action": [
6 "iam:GetRole",
7 "iam:PassRole",
8 "iam:CreateRole",
9 "iam:AttachRolePolicy"
10 ],
11 "Resource": [
12 "arn:aws:iam::<account-ID-without-hyphens>:role/outpost-v1"
13 ]
14 },
15 {
16 "Effect": "Allow",
17 "Action": [
18 "iam:GetInstanceProfile",
19 "iam:CreateInstanceProfile",
20 "iam:AddRoleToInstanceProfile"
21 ],
22 "Resource": "arn:aws:iam::<account-ID-without-hyphens>:instance-profile/outpost-v1"
23 }- Alternatively, you can create the
outpost-v1IAM role manually. The following section describes how to create the IAM role manually.
IAM Role Creation
- Click the "Roles" tab in the IAM console, and click on Create role.
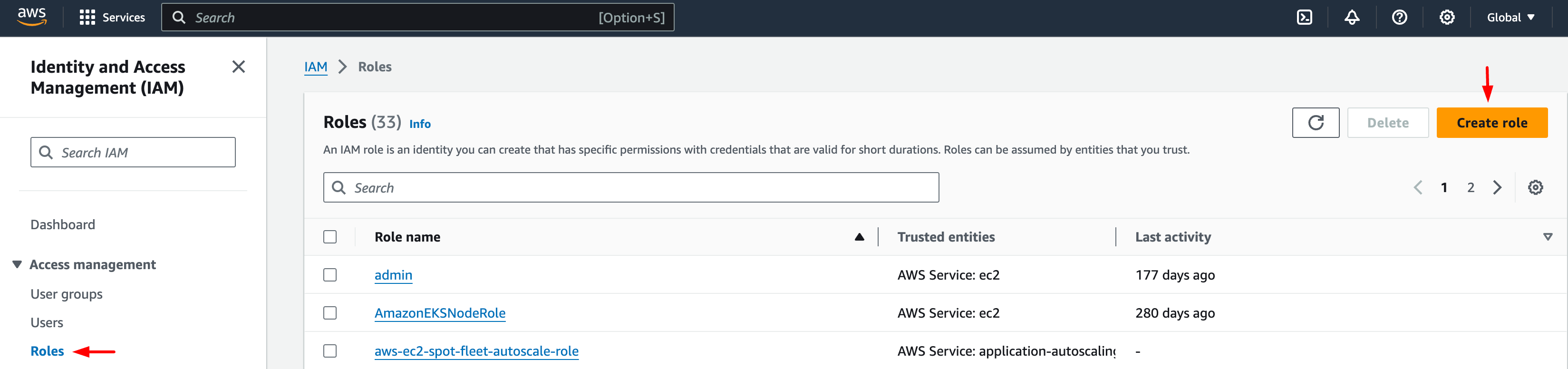
Create Roles in AWS
- Select the following entity and common use cases and click Next.
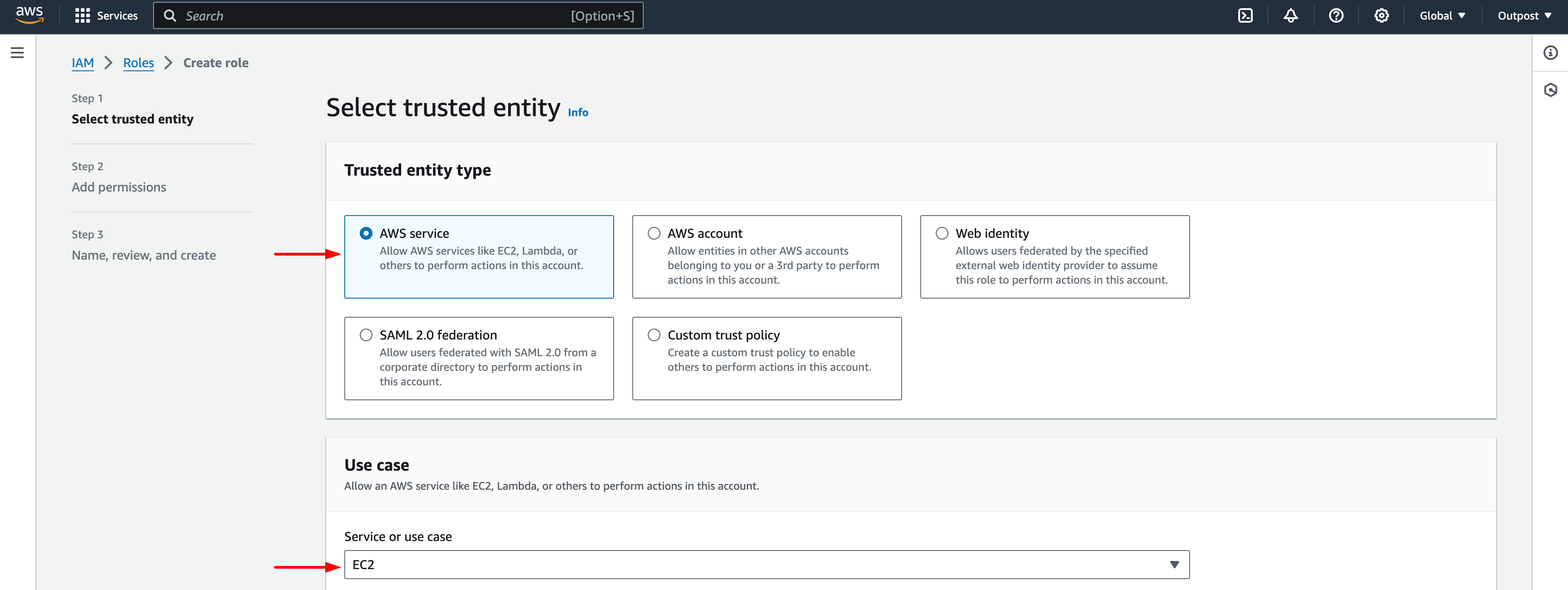
Select trusted entity
- Select the policy you created in step 4 in :ref:
User Creation <cloud-permissions-aws-user-creation>(i.e. the previous step 6) and click on Next: Tags. - Optional: If you would like to let the user access S3 buckets on the VM they created, you can additionally attach the s3 access permission to the IAM role, such as the "AmazonS3FullAccess" policy.
- Click Next, and name your role "outpost-v1". Click Create role.
Using a specific VPC
By default, Outpost uses the default VPC in each region.
To instruct Outpost to use a specific VPC, you can update deployment file:
1aws:
2 vpc_name: my-vpc-nameSee details in :ref:config-yaml. Example use cases include using a private VPC or a
VPC with fine-grained constraints, typically created via Terraform or manually.
To manually create a private VPC (i.e., all nodes will have internal IPs only), you can use the AWS console; see instructions `here